Shadow Knight Security
A cybersecurity blog site that covers a wide range of topics related to network defense, hacking, penetration testing, and security analysis.
This blog is geared towards both blue team and red team professionals who are interested in improving their skills and knowledge in the field of cybersecurity.
-
Azure Cloud Security Assessments
Categories: BlogContinue Reading: Azure Cloud Security AssessmentsAs a cybersecurity consultant who has specialized in cloud environments I understand the importance of conducting regular security assessments on Azure environments. This ensures that…
-
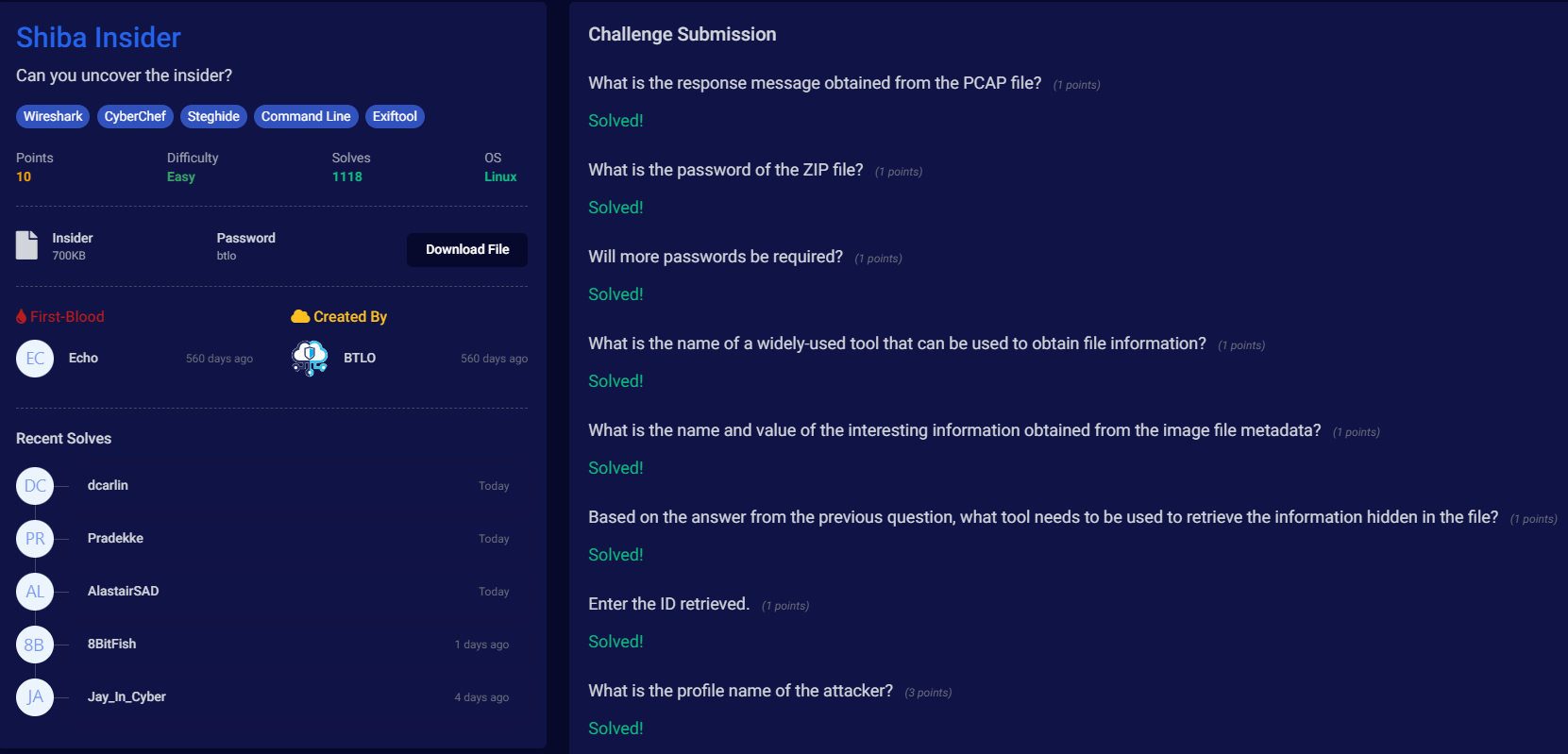
BTLO: Shiba Insider Walkthrough
Continue Reading: BTLO: Shiba Insider WalkthroughThis is a writeup of the Shiba Insider Challenge on Blue Team Labs Online. This challenge entails Wireshark PCAP analysis, exif data analysis, and steganography….
-
SOC: Dark Radiation Ransomware Response and Analysis
Categories: Blue TeamContinue Reading: SOC: Dark Radiation Ransomware Response and AnalysisSo you’ve found yourself in the unfortunate situation where one (or more) of your internal machines has been compromised by ransomware. What do you do?…
-
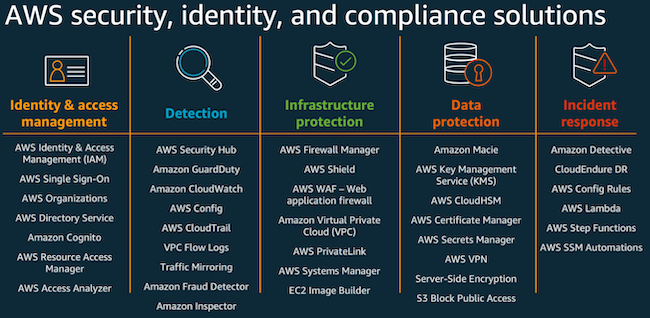
Guide: Securing AWS Cloud Environments
Categories: Blue TeamContinue Reading: Guide: Securing AWS Cloud EnvironmentsThe concept of cloud security is an ambiguous one and means different things to different people. Most people tend to think cloud security is the…
-
IOT (In)Security
Categories: Blue TeamContinue Reading: IOT (In)SecurityWhat could possibly go wrong? We live in a society that is rapidly increasing its technological profile for the purposes of increased convenience. We are…
-
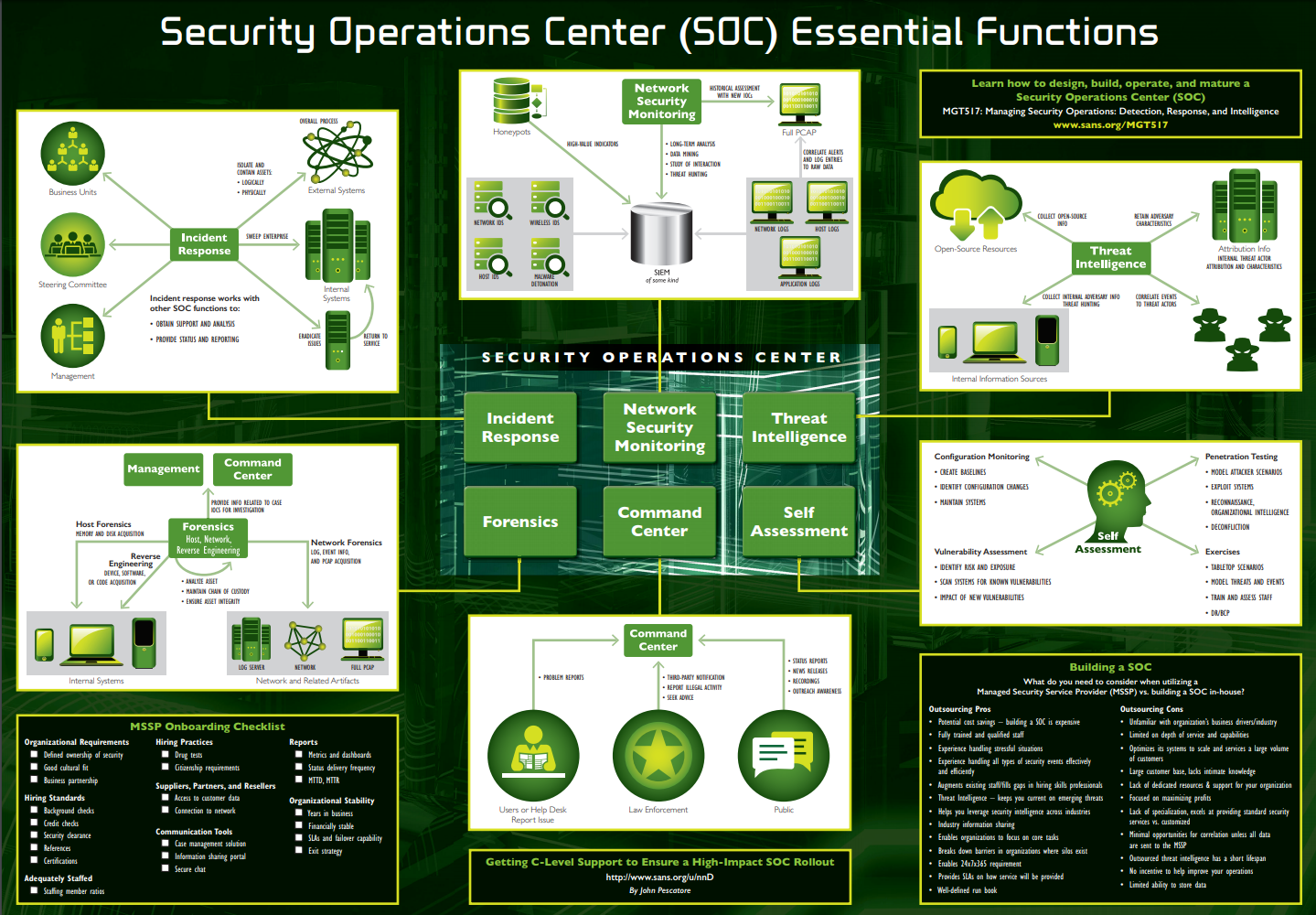
Security Operations Overview
Categories: Blue TeamContinue Reading: Security Operations OverviewPurple by default In a world where we’re hired to be a traditional blue teamer, if we have the drive, we often have the opportunity…
-
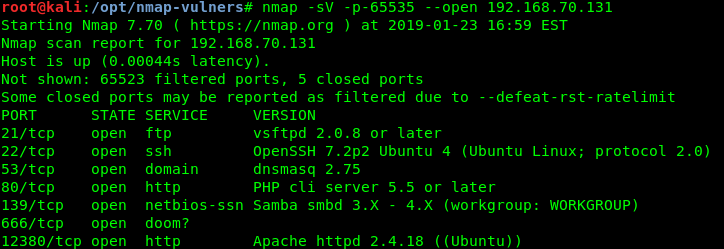
Vulnerable Machine – Stapler
Categories: Red TeamContinue Reading: Vulnerable Machine – StaplerExploit Method 1 Walkthrough Stapler is a “boot to root” VM hosted on the Vulnhub website. Boot to root challenges are designed for penetration testers…