As a cybersecurity consultant who has specialized in cloud environments I understand the importance of conducting regular security assessments on Azure environments. This ensures that any potential security threats are detected and remediated promptly, minimizing the risk of a security breach. The Azure landscape, tooling, and even their service naming schema is ever evolving and ever changing and how we perform assessments changes year upon year and ultimately becomes easier.
Here is some guidance for security professionals to conduct security assessments on their own Azure environments and ensure that they are configured securely:
Review Microsoft Defender for Cloud Recommendations:
This is the new experience that has largely replaced Azure Security Center, and provides security recommendations for your Azure environment, based on industry best practices and compliance standards. Review these recommendations regularly and remediate any issues identified. This is the central nexus for your Azure Secure Score, and as you remediate findings your score will improve. For those of you with Amazon Web Services (AWS) cloud experience, this is similar to the Security Hub.
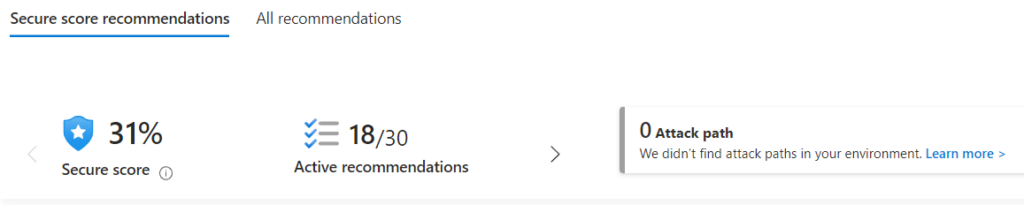
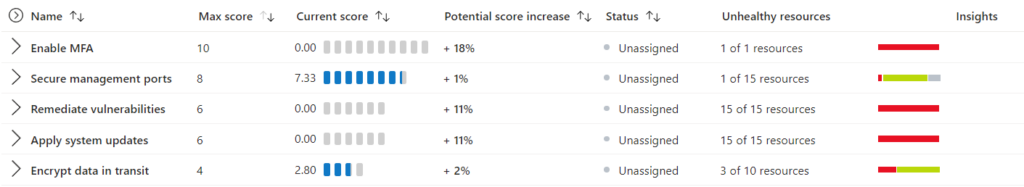
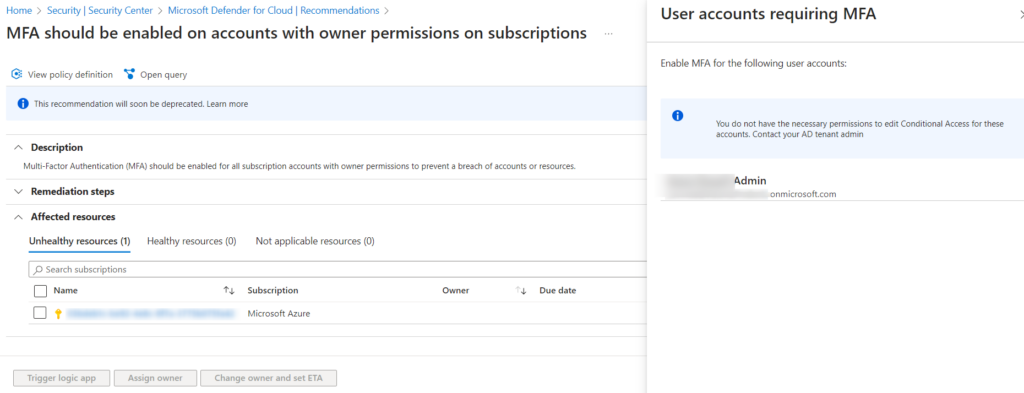
Use Third Party Tools:
Use third party tools such as Tenable Nessus (Paid) or ScoutSuite (FOSS) to audit your environment from a different perspective, and against different baselines. I always recommend using reputable tools from github developers as a first course of action prior to looking to spend valuable capital on a professional grade tool. Often, the more popular and maintained open source solutions are as good as the professional ones. Below is an example of some of the recommendations from ScoutSuite, my own tool of choice. It’s a great complimentary tool to Microsoft Defender for Cloud, as it gives you a quick overview of what remediation actions need to be taken and breaks them down by category.
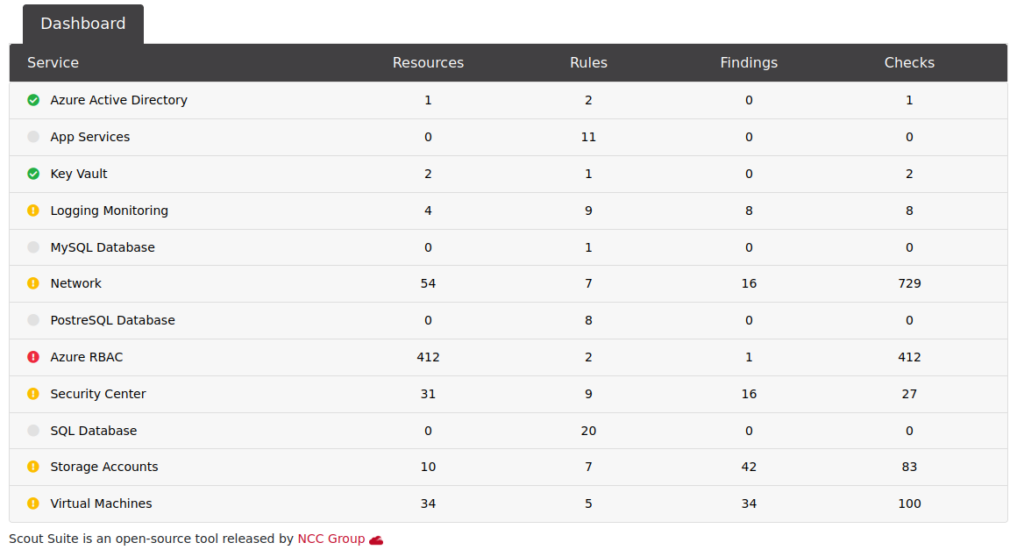
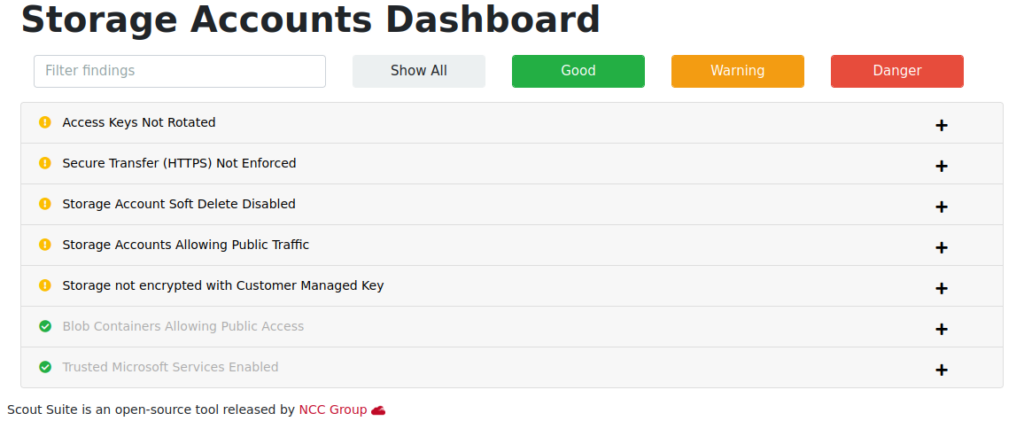
Conduct vulnerability scans:
Use Azure Security Center to conduct vulnerability scans on your Azure environment. These scans will identify any vulnerabilities in your environment, allowing you to remediate them before they are exploited by attackers. Alternatively, use a third party tool such as Tenable Nessus or Rapid7 Nexpose.
Monitor Azure activity logs:
Azure Activity Logs provide a detailed record of all activity within your Azure environment. Regularly reviewing these logs can help you identify any suspicious activity, such as failed logins or unusual resource changes.
Use Azure Policy:
Azure Policy allows you to define and enforce policies for your Azure environment. This can help ensure that resources are deployed in a secure manner and that compliance requirements are met. Ensure that Azure Policies are defined for any regulatory frameworks your company is held to, such as SOX, SOC 2, NIST 800-53, FedRAMP, etc. Microsoft provides guidance as to which built in policy rules should be selected to meet each framework. A quick note to those familiar with AWS Config; Azure Policy Initiatives are similar to AWS Conformance packs, and Azure Policy is similar to individual Config rules.
Here is an example of the Policy Initiatives available in Azure Policy and a sample set of NIST 800-53 Policy Definitions.
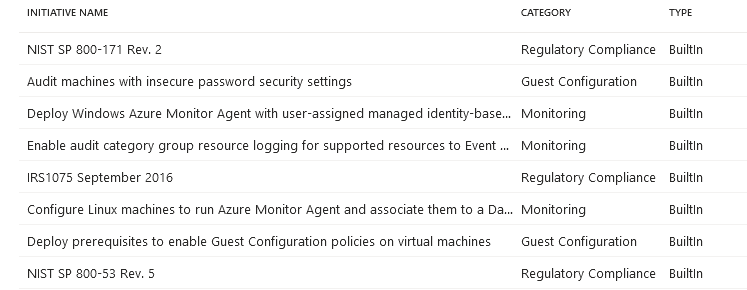
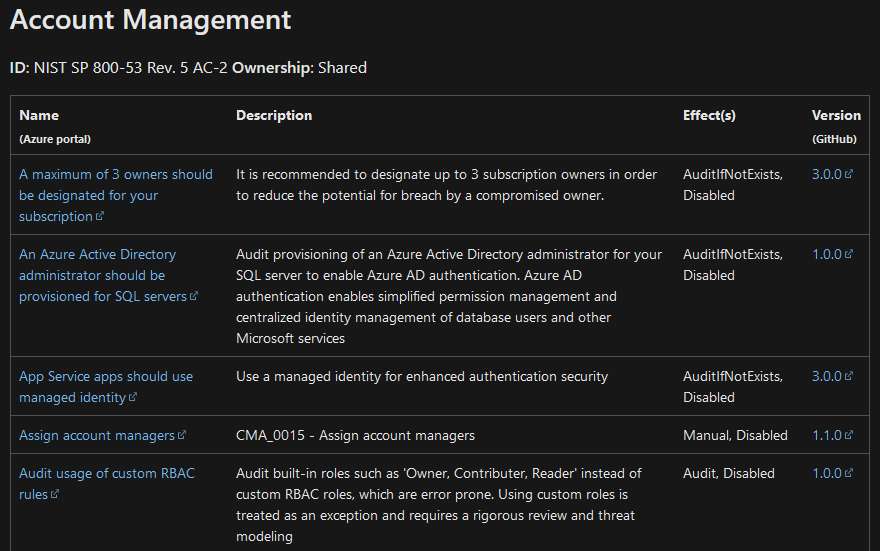
By following these tips, security professionals can conduct security assessments on their own Azure environments and detect and remediate potential security threats. Regular assessments and remediation efforts are key to maintaining a secure Azure environment and protecting against security breaches.


Leave a Reply